Kaspersky Threat Attribution Engine
An unrivaled malware analysis tool providing insights into the origin of malware and its possible authors
![]()
Sorry, this product is no longer available, please contact us for a replacement.
Overview
Tracking, analyzing, interpreting and mitigating constantly evolving IT security threats is a massive undertaking. Setting aside all the hype, threat intelligence is of true value, and threat attribution is a critical element here.
There’s a good reason why threat attribution plays such a significant role in cybersecurity. The average time lag between detecting and responding to highly sophisticated threats can be frustratingly protracted, due to the complex investigation and reverse engineering processes involved. In many cases, this delay can give attackers enough time to reach their goals. Correct and timely attribution helps not only to shorten incident response times from hours to minutes, but also to reduce the number of false positives.
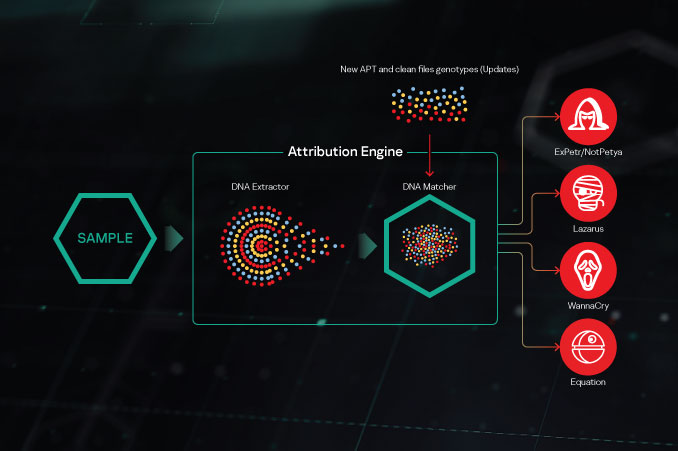
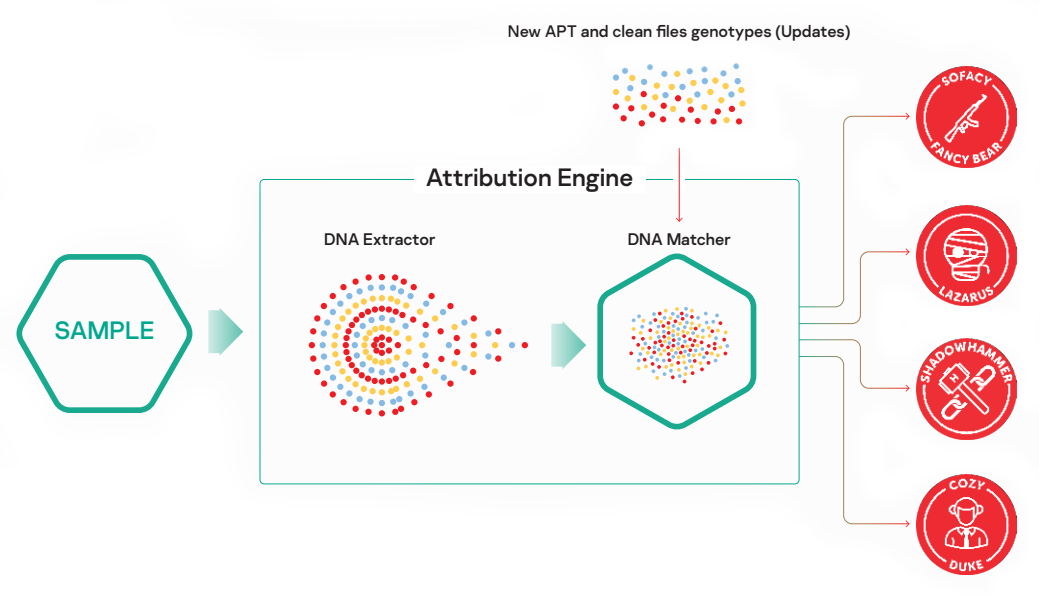
Identifying a targeted attack, profiling the attackers and creating attribution factors for the different threat actors is a long and complex job, which can take years. Creating a working attribution also requires a large amount of data accumulated over time, as well as a highly-skilled team of researchers with the relevant investigation experience. These researchers will commonly follow the activity of different groups, and populate a database with all the pieces of information accrued. This database then becomes a valuable resource that can be shared as a tool.
Kaspersky Threat Attribution Engine incorporates a database comprising APT malware samples and clean files gathered by Kaspersky experts over the last 25 years and more. We track 1100+ threat actors and campaigns and release 120+ threat intelligence reports a year. Our ongoing research supports an APT collection which contains some 83,000 files. This improves false flag detection and, in conjunction with the use of automated tools, results in outstandingly accurate levels of attribution.
The product offers a unique approach to comparing similar samples while ensuring near-zero false positive rates. Any new attack can quickly be linked to known APT malware, previous targeted attacks and hacker groups, helping you to distinguish high-risk threats from less serious incidents, so you can take timely protective measures to prevent an attacker from gaining a foothold in your system.
Product highlights:
- Provides instant access to a repository of curated data about thousands of APT actors, samples and broader threats (via the anti-virus engine)
- Allows efficient automated or manual threat prioritization and alert triage
- Functionality to add private actors and samples, educating the product to detect samples that are similar to files in your private collection
- Manual sample upload and an enhanced REST API for integration with automated workflows
- Can be deployed in a secure, air-gapped environment, to protect your systems and data as well as meeting any compliance requirements
- Supports deployment on Amazon Web Services (AWS) enabling quick product setup and saving costs as no need to invest in hardware upfront
- Export to YARA rules for further automated search/scanning for similar files or integration with third-party solutions
- Export to STIX 2.1 format (TXT and JSON formats are also supported) for further automated analysis of security logs or integration with third-party solutions/ security controls
- Functionality for unpacking passwordprotected archives with custom passwords
- Access to documentation and End User License Agreement (EULA) in the web interface
- Ability to attribute in parallel files that are sent for analysis in one request
Additional benefits:
- Kaspersky Threat Attribution Engine calculates the reputation score of the sample and reveals its genetics and code attribution. This provides insights into the origin of the sample and can enable its attribution to possible authors.
- Your security team can add your own private attribution entities and related samples to the Kaspersky Threat Attribution Engine database. The team can then educate the application to attribute submitted samples to these private attribution entities and samples.
- With Kaspersky Threat Attribution Engine, the attribution process takes only seconds, compared to the months and years required in the past.
Kaspersky Threat Attribution Engine further extends and strengthens the Kaspersky portfolio for national cybersecurity agencies and commercial Security Operations Centers (SOCs) by supporting them in establishing an effective incident management process.
Kaspersky Threat Attribution Engine significantly improves security operations, helping to:
- Rapidly attribute files to known APT actors, revealing the motivations, methods and tools behind cyber incidents;
- Quickly evaluate whether you are the target of an attack or a side victim, so you can initiate the proper containment and response procedures;
- Ensure effective and timely APT threat mitigation based on actionable threat intelligence provided in Kaspersky APT Intelligence Reporting.
Prior knowledge as a strategic advantage
While conducting their operations, hackers normally follow a set of tactics, techniques and procedures. Cyber security experts are able to identify threat actors by studying these elements. Effective and efficient attribution always involves a highly-skilled team of researchers with experience in forensics and investigation, and is based on many years’ worth of accumulated data. This kind of database become a valuable resource that can be shared as a tool.
![]()
Threat Attribution
Quickly links a new attack to known Advanced Persistent Threat (APT) malware, helping to see the high-risk threat among less serious incidents and take timely protective measures.
![]()
Timely Response
Enables effective investigation, containment and response based on knowledge of the tactics, techniques and procedures specific to the threat actor.
![]()
Self-learning Engine
Allows security teams to add private actors and objects to its database and ‘educate’ the product to detect samples that are similar to files in their private collections.
![]()
Privacy and Compliance
Can be deployed in secure, air-gapped environments to protect your systems and data as well as meet any compliance requirements.
Suitable for
Kaspersky Threat Attribution Engine is ideal for:
- Government
- Managed Security Service Providers
- Financial Services
- Enterprises
Pricing Notes:
- Pricing and product availability subject to change without notice.