Overview
If your business has ever suffered a Distributed Denial of Service (DDoS) attack, you’ll already know that the financial and reputational costs can be devastating. However, even if your business has been lucky enough to escape the attentions of the cybercriminals and hackers that launch these attacks, the outlook for the future may not be so positive.
The volume and severity of attacks is increasing
Unfortunately, in recent years, the cost of launching a DDoS attack has fallen significantly – and that means more attacks are being initiated than ever before. At the same time, today’s attacks are more complex and they’re at a scale that can overwhelm the target business’s communications bandwidth in just a few seconds – almost instantly debilitating vital, internal business processes and totally disabling the victim business’s online presence.
With all sizes of business relying on their IT infrastructure and website to underpin almost all of their mission-critical processes, extended downtime – that can result from a DDoS attack – is not an option. Clearly, with the volume, scale and severity of modern attacks, it’s no longer viable for any business to put off any thoughts of DDoS protection and mitigation until the point at which their infrastructure is already under attack. Instead, businesses – and public sector organizations – need to be aware of the threats and ensure they have adequate DDoS defense measures in place.
'Forewarned is forearmed'
Every business needs to have an anti-DDoS strategy – ready to ‘go live’ as soon as an attack is detected. Then, in the event of an attack, the business will be able to mitigate the effects – without delay – in order to:
- Minimize downtime for business-critical infrastructure & processes
- Ensure customers can continue to access online services
- Maintain productivity for employees
- Minimize reputational damage
DDoS Attack Methods
Cybercriminals and hackers are using a number of different techniques to implement DDoS attacks that disable or overload the target business’s IT infrastructure.
Volumetric Attacks
These attacks are increasingly common. By generating traffic levels that exceed the target business’s available bandwidth, the attack saturates the capacity of the victim’s corporate Internet connection – and that disables or delays all online activities.
Application Layer Attacks
Application layer attacks try to crash the servers that are running vital applications – such as the web servers that the victim’s online presence depends on.
Other Infrastructure Attacks
Attacks that aim to disable network equipment and / or server operating systems can totally halt the operation of key business processes.
Hybrid Attacks
Cybercriminals also launch complex attacks that combine several methods – including volumetric, application layer and infrastructure attack techniques.
The Total Defense and Mitigation Solution
Kaspersky DDoS Protection delivers a total, integrated DDoS attack protection and mitigation solution that takes care of every stage that’s necessary to defend your business. From continuous analysis of all of your online traffic, through to alerting you about the possible presence of an attack and then receiving your redirected traffic, cleaning your traffic and returning ‘clean’ traffic to you, Kaspersky DDoS Protection provides everything your business needs to defend against – and mitigate the effects of – all types of DDoS attacks.
Kaspersky DDoS Protection Includes:
- Kaspersky Lab sensor software – that runs within your IT infrastructure
- The services of our global network of data traffic 'cleaning centers'
- Support from our Security Operations Center and DDoS protection experts
- Detailed, post-attack analysis and reports
How Kaspersky DDoS Protection Works
Kaspersky Lab’s sensor software collects information about all of your communications traffic – 24x7x365. The sensor is installed as close as possible to the resource that you wish to protect – and it continuously gathers data about your traffic, including:
- Header data
- Protocol types
- Number of bytes sent and received
- Number of packets sent and received
- Activities and behavior – of every visitor to your website
- All metadata about your traffic
All of this information is sent to Kaspersky Lab’s cloud-based servers, where it is analyzed so that we can build up profiles of how typical visitors behave and profiles of your typical traffic – and how that traffic can vary according to the time of day and the day of the week, plus how special events can affect your traffic patterns. With this detailed understanding of your ‘normal traffic conditions’ and ‘normal visitor behaviors’, our cloud-based servers can accurately assess your live traffic conditions – in real time – and rapidly identify anomalies that can indicate that an attack has been launched against your business.
In addition, our threat intelligence experts continuously monitor the DDoS threat landscape – in order to identify new attacks. This specialist intelligence helps to ensure Kaspersky Lab customers benefit from a rapid response to the launch of an attack.
Avoiding false alarms...Then cleaning your traffic
As soon as a possible attack against your business is identified by our servers or our intelligence experts, Kaspersky Lab’s Security Operations Center will receive an alert. To help avoid false alarms – and unnecessary disruptions for your business – Kaspersky Lab engineers check to confirm that the traffic anomaly or suspicious behavior has resulted from a DDoS attack. Then, our engineers immediately contact your business – to recommend that your traffic is redirected to our network of cleaning centers.
During the attack, with all of your traffic now passing through one of our cleaning centers:
- Your infrastructure is no longer being overwhelmed by the sheer volume of ‘junk traffic’
- Our cleaning process discards all junk traffic
- Legitimate traffic is delivered back to you – from our network of cleaning centers
… and the entire process is totally transparent to your employees and customers.
Setting up protection is quick and easy
When you choose Kaspersky DDoS Protection, there’s a small number of set up tasks before your 24x7 monitoring – and your ‘live attack’ communications channels – are established. Kaspersky Lab – and its partners – can take care of as much or as little of the set up process as you require.
If you require a turnkey solution, Kaspersky Lab and its partners can cover the vast majority of set up procedures – including:
- Installing the sensor software and hardware on your site
- Setting up traffic redirection to our cleaning centers
- Setting up ‘clean’ traffic delivery to your business
… then, all you’ll need to provide is a separate Internet channel to the sensor – so that Kaspersky DDoS Protection can continue to collect data when your main Internet channel has been disabled by an attack.
The senser - enabling 24x7 monitoring
Kaspersky Lab’s sensor software is supplied complete with a standard Ubuntu Linux operating system. Because the sensor software runs on a standard x86 server – or on a virtual machine* – there’s no special hardware for you to maintain. Because the sensor is connected to the SPAN (Switched Port Analyzer) port, it’s able to get the best possible view of all traffic that’s flowing into and out of the resource that it’s protecting. As soon as the sensor is connected to your infrastructure, it starts collecting data on your incoming and outgoing traffic. It analyses each packet’s headers and sends information to the Kaspersky DDoS Protection cloud servers – where we build statistical profiles of ‘normal traffic behavior’ and ‘normal visitor behavior’ for your business.
In order to maintain privacy for your communications – and help with your compliance commitments – the sensor does not capture the content of any of the messages within your communications traffic. The sensor only gathers data about your traffic – so the confidentiality of your messages is never compromised by any of Kaspersky DDoS Protection’s processes.
Generic Routing Encapsulation (GRE) Virtual Tunnels
Whichever redirection method is best for your business, GRE virtual tunnels are used to enable communication between your border gateway – or router – and each relevant Kaspersky DDoS Protection cleaning center.
In the event of a DDoS attack being launched against your business, all of your traffic can be rerouted to one of our cleaning centers. The GRE virtual tunnels are then used to deliver the cleaned traffic – from our cleaning centers, to your business.
Choosing between BGP and DNS
Whether you set up your traffic redirection via BGP or DNS, will largely depend on the nature of your corporate IT and communications infrastructure:
- For BGP, you’ll need to have:
- A provider-independent network – that includes the resources that you wish to protect
- An autonomous system … and most large businesses are able to meet these criteria.
- For DNS, you’ll need to be able to:
- Manage your own domain zone for the resources that you’re looking to protect
- Set the Time to Live (TTL) for DNS records to 5 minutes
Generally, during an attack, the BGP method achieves faster redirection of traffic – so BGP is often the preferred method for most businesses.
Why It Matters
How could DDOS affect you?
When hackers or cybercriminals launch a Distributed Denial of Service (DDoS) attack, the damage – and the costs – can be devastating for the business that's being targeted.
DDoS attacks are used to disable the targeted organization's online presence or key business processes – and that can have long lasting impact for the victim.
Is your business doing all it can to achieve effective DDoS attack protection?
Keeping your business online
With online activities playing an increasingly important role in virtually every business's day-to-day interactions with customers, suppliers and employees, no business can afford to ignore today's growing DDoS risks. Your online services – and all of your IT infrastructure – are just too important to leave unguarded:
- Your customers are more demanding than ever
- They expect 'always on' access to products and services – and that means unplanned downtime isn't an option if your business is going to keep hitting its targets for customer satisfaction levels.
- Your own team needs reliable access to key services
- Many of your employees simply can't perform their work tasks if any of your critical systems are taken out of action by a DDoS attack.
- The effects of an attack can be far-reaching
Even though the attack may be targeting a specific element of your infrastructure, it could affect other areas of your business. For example, an attack against a bank's internal systems could also disable its entire network of ATMs (Automated Teller Machines).
Financial damage... and more
The direct financial costs of recovering from a DDoS attack can be massive… and the reputational damage can keep adding to those costs over the long term:
- Direct financial costs
- Failed sales transactions – during downtime periods
- Failed online banking transactions – with possible penalties
- Your own team needs reliable access to key services
- Negative publicity that dissuades existing customers and potential clients
- Damage to your business brand – that could take years to recover from
Confusion causes even more damage
If your business is subjected to a DDoS attack, it could also suffer additional losses that result from misconceptions about exactly what a DDoS attack is – and how it could affect your customers. Even though DDoS attacks are unlikely to have any effect on your customers´ security, can you be sure your customers will understand this?
Whenever customers hear about a ´security incident´ – any security incident – some may fear that their confidential information, bank details and credit card numbers could be at risk. Even though these fears may be totally illogical – and stem from customers´ misunderstandings about the nature of DDoS attacks – your business could still suffer.
Threats
Scale of the threats
DDoS attacks are nothing new. They've been a threat for many years. However, the level of danger is much higher than in previous years. Recently, because the cost of launching a DDoS attack has reduced, the volume of attacks has rapidly increased. At the same time, today's attacks are much more complex and sophisticated – so you need to do much more to defend against them.
Yesterday's defenses can't protect you today
The scale and sophistication of DDoS attacks has evolved. Unfortunately, this means today's complex attacks are:
- Much more difficult to guard against
- Even harder for a business to recover from
In addition, the sheer scale of a typical attack can rapidly overwhelm the target's infrastructure. With today's attacks often running at 80 – 100 Gb per second, the bandwidth of typical corporate networks can be saturated in just a few seconds.
All of this means that the simple prevention techniques – that were still effective only a few years ago – no longer offer adequate DDoS attack protection. Businesses are no longer able to defend against attacks, without using specialist defense services. The threats have become more devious… so your protection measures have to be even more capable.
How DDoS attacks overwhelm businesses
There are many different ways for hackers to overload the target business's IT infrastructure – to cause a 'denial of service'. Some of the most common types of attack include:
- Volumetric attacks
These attacks try to saturate the capacity of your corporate Internet connection – by generating traffic levels that exceed your available bandwidth.
- Application and infrastructure attacks
Application layer attacks seek to crash servers that are running vital applications – such as the web servers that your online presence depends on. Other infrastructure-based attacks may try to disable your network equipment and / or server operating systems.
- Hybrid attacks
These can be particularly challenging – as they combine volumetric attack methods and application layer or infrastructure attack techniques.
DDoS attack protection… the essentials
To ensure your business is adequately defended against DDoS attacks, you need a DDoS attack prevention solution that helps you to:
- Detect any new attack as rapidly as possible
So you can defend your business very soon after the hacker launches the attack against your business
- Mitigate the effects of the attack as rapidly as possible
So your business can minimize – or totally prevent – any disruption to its normal business activities
Solutions
Kaspersky Lab's Solution
Kaspersky DDoS Protection gives you a total, integrated solution that includes everything your business needs to defend against DDoS attacks:
- Special sensor software* – for installation on your site
- Access to a resilient, distributed network of 'cleaning centers'
- Advanced intelligence about the latest DDoS attacks
- The services of our Security Operations Center
- Extensive support – including direct access to DDoS protection experts
- Post-attack analysis and reports
- ...all backed up by a stringent Service Level Agreement.
How we protect you
Kaspersky DDoS Protection takes care of every stage in defending your business – from ongoing 24x7 analysis of your traffic, through to alerting you about the possible presence of an attack and then redirecting your traffic, cleaning your traffic, returning 'clean' traffic to you… and, finally, giving you post-attack reports & analysis.
Unlike other vendors' offerings, Kaspersky Lab's solution fights DDoS attacks on two fronts:
- Special defense infrastructure – including our sensor software – running on your site – and systems running at a network of Kaspersky Lab sites
- Kaspersky Lab DDoS intelligence – for earlier detection of DDoS attacks
Special sensor
Kaspersky Lab provides special sensor software that runs at your site – and, as soon as it's installed, the sensor software starts to collect statistics and build usage profiles that help it to protect your business.
It monitors your traffic and – by continually building up statistical data and behavioral analysis data – the sensor continuously enhances its ability to detect even very subtle anomalies that are characteristic of the start of a DDoS attack.
Because the sensor software runs on a standard x86 server or a virtual machine, there isn't any non-standard hardware for you to maintain.
Cleaning Centers
In the event of a DDoS attack, we'll alert you and give you the option of redirecting your traffic to Kaspersky Lab's Cleaning Centers – and then having only 'clean traffic' returned to you.
We've invested in a distributed network of Cleaning Centers – to deliver a highly resilient and scalable traffic cleaning capability.
DDoS attack intelligence
Kaspersky Lab's malware experts use sophisticated methods to monitor the DDoS threat landscape and keep ahead of the hackers – so that we can achieve earlier detection of DDoS attacks.
Because traditional DDoS prevention vendors don't have security intelligence departments, this proactive layer of protection cannot be delivered by these vendors.
*The sensor software runs on a standard x86 server or on a virtual machine. If you require a new server, it can be supplied by one of Kaspersky Lab's partners.
Benefits
Solution benefits
Defending against the most complex DDoS attacks doesn't have to be a complex task for your business.
When you choose Kaspersky DDoS Protection, you're effectively 'giving your entire DDoS attack protection problem to Kaspersky Lab'.
With Kaspersky Lab's integrated defenses on board, your IT and security teams are free to focus on your core business activities – safe in the knowledge that you've got multi-layered defenses against the most sophisticated attacks.
Expertise is essential
Unlike virus attacks that tend to propagate automatically, DDoS attacks rely on human expertise – and that can make DDoS attacks particularly difficult to defend against… unless you have the Kaspersky Lab experts helping to protect you.
For virtually every DDoS attack:
- Hackers research their target
The attackers assess vulnerabilities within the target business's online presence – and then preselect the attack tools that are most likely to achieve the hacker's malicious objectives.
- Cybercriminals adapt their tactics
Working in real time – during the attack – hackers constantly change tactics, adapt their approach and select different tools… in order to maximize the damage they can inflict.
Because real people are constantly fine tuning almost every 'live' DDoS attack, you need real DDoS mitigation experts fighting against your attackers in real time… and that's exactly what Kaspersky DDoS Protection delivers.
Inline versus non-inline
In the past, some vendors proposed the use of a hybrid defense that included an inline appliance and remote cleaning centers. The inline appliance would continually intercept the business's traffic and provide some level of defense for small attacks – and only suggest redirecting traffic if a large attack was detected. However, with the vast majority of today's attacks now able to overwhelm the capacity of both an inline appliance and the targeted business's Internet connection – within a few seconds – this approach is now outdated, and it can introduce delays before traffic is redirected to a cleaning center.
Kaspersky DDoS Protection uses a non-inline sensor that continuously monitors your traffic – without intercepting it. As soon as the sensor detects a potential attack, you have the option of redirecting all traffic to one of Kaspersky Lab's cleaning centers.
Because Kaspersky Lab's solution totally avoids the use of inline appliances:
- You have greater control over whether your traffic is redirected to cleaning centers
- You benefit from DDoS protection that also achieves a lower rate of false positives
Greater visibility – across your business
Although no one can stop cybercriminals targeting your business, Kaspersky Lab is ideally placed to deliver a rapid response to any DDoS attack. Then – after we've defended you against the attack and mitigated the effects – we'll deliver detailed, post-attack analysis and reporting on exactly:
- What happened
- How long it lasted
- How Kaspersky DDoS Protection dealt with the attack
...so every level of your business benefits from clear visibility of the issues.
Reasons
Kaspersky Lab - The Reasons
Kaspersky DDoS Protection combines three protection techniques – to deliver more rigorous DDoS attack protection:
- Statistical analysis – of your online traffic helps us to build profiles and detect deviations
- Behavior analysis – monitors your website's visitors, so we can identify abnormal behavior
- Advanced DDoS intelligence – that only our solution can offer – enhances detection rates
Far-ranging protection
Whereas some vendors can protect against volumetric attacks and other vendors' offerings are more suited to defending against application layer attacks, Kaspersky Lab provides effective protection and mitigation for all types of DDoS attacks, including:
- Volumetric attacks
- Application layer attacks
- Infrastructure attacks – against networks & operating systems
- Hybrid attacks… and more
… so, whatever technique the attackers use, Kaspersky DDoS Protection safeguards your business.
Unique combination of skills
Because today's DDoS attacks are much more sophisticated, an intelligence-led approach to defense is vitally important. No other DDoS prevention solution vendor has our background in IT security – so no other vendor has a dedicated attack intelligence team.
Because we're the first anti-malware vendor to offer a DDoS protection solution, we're able to provide a unique combination of statistical analysis, behavior analysis and DDoS attack intelligence… for more thorough defense.
Improved sensitivity – for improved detection
Some vendors are only able to provide broad monitoring of the entire communication channel. However, Kaspersky Lab's solution is capable of granular analysis – so we can detect even smaller deviations from normal traffic and normal behavior.
In addition, we use special techniques that let us filter traffic at points that are as close as possible to the source of an attack.
Integrated teams – for a tightly integrated solution
Because all of the software inside Kaspersky Lab's DDoS Protection solution – and other security products – is developed by the company's own, in-house experts:
- We have full control of the development cycle
- We can react more rapidly to changes in the DDoS attack landscape
Furthermore, our DDoS Emergency Response Team works very closely with Kaspersky Lab’s lead engineers and solution architects. Communication lines are short and feedback loops are very responsive – so we can rapidly deliver new plug-ins that defend against new application layer attacks.
How It Works
How BGP Redirection Works
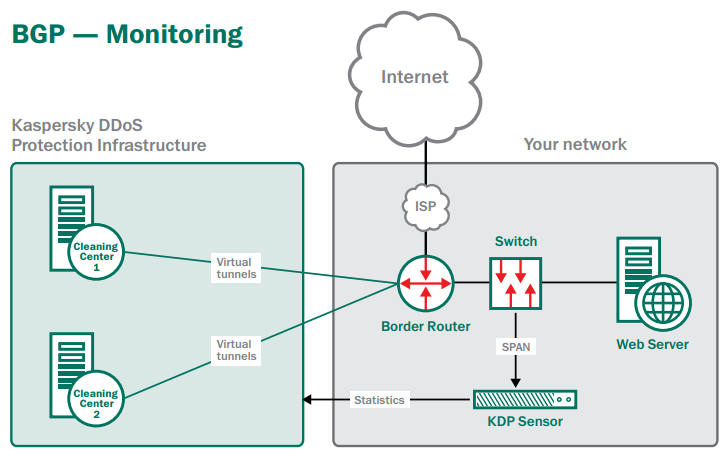
Monitoring
In monitoring mode, all of your traffic is delivered directly to your business. However, the GRE virtual tunnels are in ‘live’ operation – with your routers and our BGP routers frequently exchanging status information… so the Kaspersky DDoS Protection cleaning centers are ready to receive your redirected traffic whenever necessary.
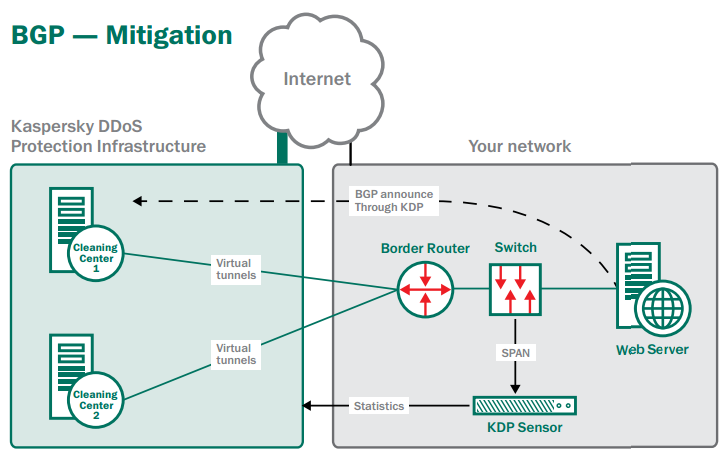
During an attack
When a traffic anomaly is identified by Kaspersky Lab’s sensor – and the start of an attack is confirmed by Kaspersky Lab’s engineers – you can choose to redirect all of your traffic to a Kaspersky DDoS Protection cleaning center. Throughout the attack, the Kaspersky Lab sensor will continue to gather information and send it for analysis by the cloud-based Kaspersky DDoS Protection servers.
After an attack
When the attack has ceased, your traffic is once more sent direct to your business. The sensor continues to gather data about your traffic – and constantly passes this data to our cloud-based servers, so that we can continuously refine our behavior profiles for your normal traffic conditions. The virtual tunnels remain live – exchanging status information between your routers and Kaspersky Lab’s routers – so that Kaspersky DDoS Protection is ready to act if another attack is launched against your business and you choose to redirect your traffic again.
Kaspersky Lab’s experts will also provide you with detailed, post-attack analysis and reporting on exactly:
- What happened during the attack
- How long the attack lasted
- How Kaspersky DDoS Protection dealt with the attack
How DNS Redirection Works
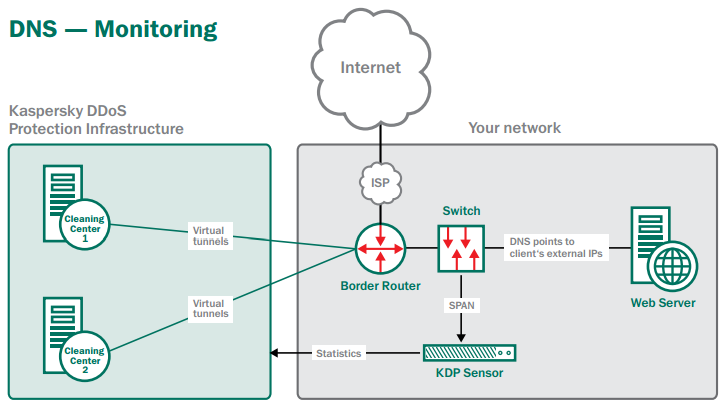
Monitoring
During initial set up, Kaspersky Lab allocates one of its pool of Kaspersky DDoS Protection IP addresses to your business. This address will be used in the event of an attack. In monitoring mode, all of your traffic is delivered directly to your business – via its normal IP address / addresses. However, the GRE virtual tunnels are in ‘live’ operation – with your routers and our BGP routers frequently exchanging status information… so the Kaspersky DDoS Protection cleaning centers are ready to receive your redirected traffic whenever necessary.
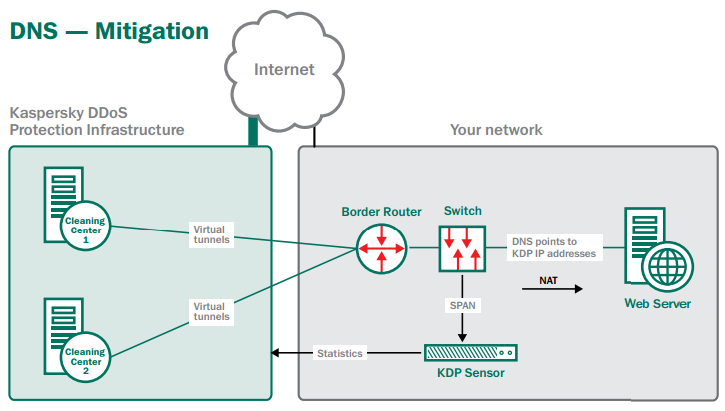
During an attack
When a traffic anomaly is identified by Kaspersky Lab’s sensor – and the start of an attack is confirmed by Kaspersky Lab’s engineers – you simply change your business’s IP address in the DNS A record… so that your business is now using the Kaspersky DDoS Protection IP address that was allocated to you during initial set up. At the same time, because hackers can directly attack your IP address, your ISP must block all traffic to your original IP address – with the exception of communications with Kaspersky Lab’s DDoS Protection infrastructure. Having changed your IP address, all your traffic is redirected to Kaspersky Lab’s cleaning centers. ‘Clean’ traffic is then delivered back to your business – from our cleaning centers – via the GRE virtual tunnels.
After an attack
When the attack has ceased, you can unblock your original IP address and change the DNS A record – so that your traffic is once more sent direct to your business. The Kaspersky Lab sensor continues to gather data about your traffic – and constantly passes this data to our cloud-based servers, so that we can continuously refine our behavior profiles for your normal traffic conditions. The virtual tunnels remain live – exchanging status information between your routers and Kaspersky Lab’s routers – so that Kaspersky DDoS Protection is ready to act if another attack is launched against your business and you choose to redirect your traffic again.
Kaspersky Lab’s experts will also provide you with detailed, post-attack analysis and reporting on exactly:
- What happened during the attack
- How long the attack lasted
- How Kaspersky DDoS Protection dealt with the attack

![]()




