Overview
Kaspersky Container Security (KCS) is a security solution that covers every stage of a containerized app's lifecycle, from development to operation. It protects your organization's business processes in line with security standards and regulations, and supports implementation of the DevSecOps approach.
Kaspersky Container Security delivers comprehensive protection from the latest cyberthreats, and automates your compliance audits, freeing up the resources of your information security team to focus on other tasks, and shortening time to market.
Kaspersky Container Security has been developed specifically for containerized environments, ensuring protection at different levels from container image to host OS.
About the solution
Containerization is one of the biggest trends in software development, accelerating the app design and delivery process. However, the architectural characteristics of containerized environments mean they can’t be secured by traditional solutions. Kaspersky Container Security is designed to cover the whole lifecycle of containerized apps from development to operation. The product protects your business processes, helping your organization to comply with security regulations and implement the principles of secure software development (DevSecOps).
Current challenges
Kaspersky Container Security helps you effectively address the challenges of:

Protecting the components of container infrastructure, which requires a specialized solution.
Traditional and open-source code analysis and endpoint protection solutions failing to address many of the information security risks inherent in containerized environments.

Development processes which must comply with your organization's security policies, and with regulatory requirements for information security.
Application
The solution allows software developers using containers to improve product security and reduce time-to-market.
For users of the software, the product helps ensure the necessary level of security, including compliance with regulatory requirements, and simplify digital transformation.
- Public sector
- Telecom
- IT
- Energy
- Finance
- Industrial enterprises
- Retail
- Extractive
Benefits
Kaspersky Container Security is a specialized containerization protection solution. It helps mitigate the risks inherent in containerized environments, frees up your information security specialist resources, and supports compliance with regulatory requirements.
Globally renowned security
Leverages international best practices in container environment security to effectively counter most cyberthreats associated with these environments.
Comprehensive protection for containerized environments
Addresses the unique needs of container environments and secures every component of the container infrastructure, from the container image registry to the orchestrator.
Compliance with regulatory requirements
Ensures app security, supporting your organization in ensuring full compliance with regulatory requirements.
Features
Kaspersky Container Security protects against information security risks inherent in containerized environments – from container image vulnerabilities to cluster node setup misconfigurations – while automating security and compliance checks.
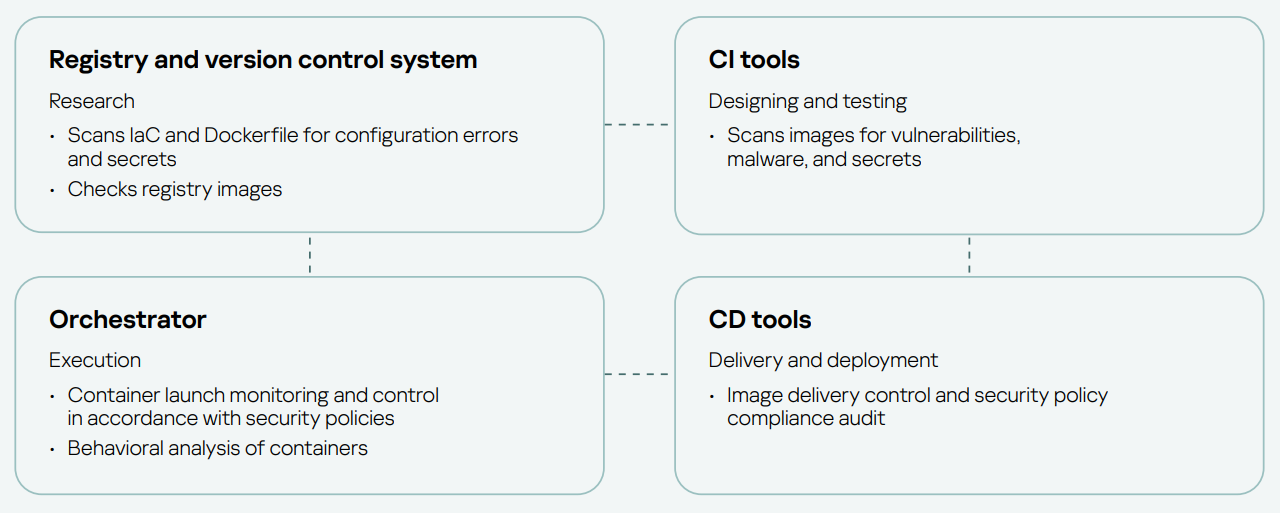
Integration into the development process
Kaspersky Container Security seamlessly integrates security into the software development process.
- Detection of vulnerabilities in running containers
Scanning running applications can identify vulnerabilities in code that can`t be detected during the build phase
- Checks container images from the registry
Automated scanning can detect irrelevant images and identify vulnerabilities, secrets and violations in configurations
- Monitors resource consumption and communications between containers
Intuitive widgets help detect suspicious activity and proactively respond to security threats
Orchestrator protection
Kaspersky Container Security provides comprehensive protection for a key component of the containerized application development and execution environment.
- Monitors authentication and authorization configuration
Centralized access control and management increases the security of not just the orchestrator, but also the organization's entire IT infrastructure
- Checks orchestrator configuration
Helps identify configuration errors, non-compliance with security policies, and unauthorized attempts to change the configuration
- Process and network control
Monitoring orchestrator activity helps to detect and stop suspicious activity both within and between clusters
Regulatory compliance audit
Kaspersky Container Security detects violations of regulatory requirements in various components of the container environment and performs audits in accordance with national and international standards.
- Checks at both orchestrator and individual container level
Security control at multiple levels allows you to address component-specific security risks
- CIS compliance verification
The ability to verify applications and infrastructure in accordance with the methodologies of international organizations helps implement global best practices for information security
- Vulnerability analysis based on NIST database
Enhances corporate security through the timely detection of vulnerabilities in the container infrastructure
Visualization and inventory of cluster resources
Clear and intuitive widgets and infographics help not only to monitor product status, but also to detect security incidents based on indirect indicators.
- Monitors cluster status
Visualization of processes and cluster status provides a high level of awareness and readiness to respond to potential incidents
- Fully customized widgets to reveal cross-section data
Information displayed in widgets provides a detailed visualization of the processes taking place in the product and the protected infrastructure
- Resource inventory
Compiling a "catalog" helps identify unaccounted resources and their owners, which increases overall security and helps close gaps
Architecture
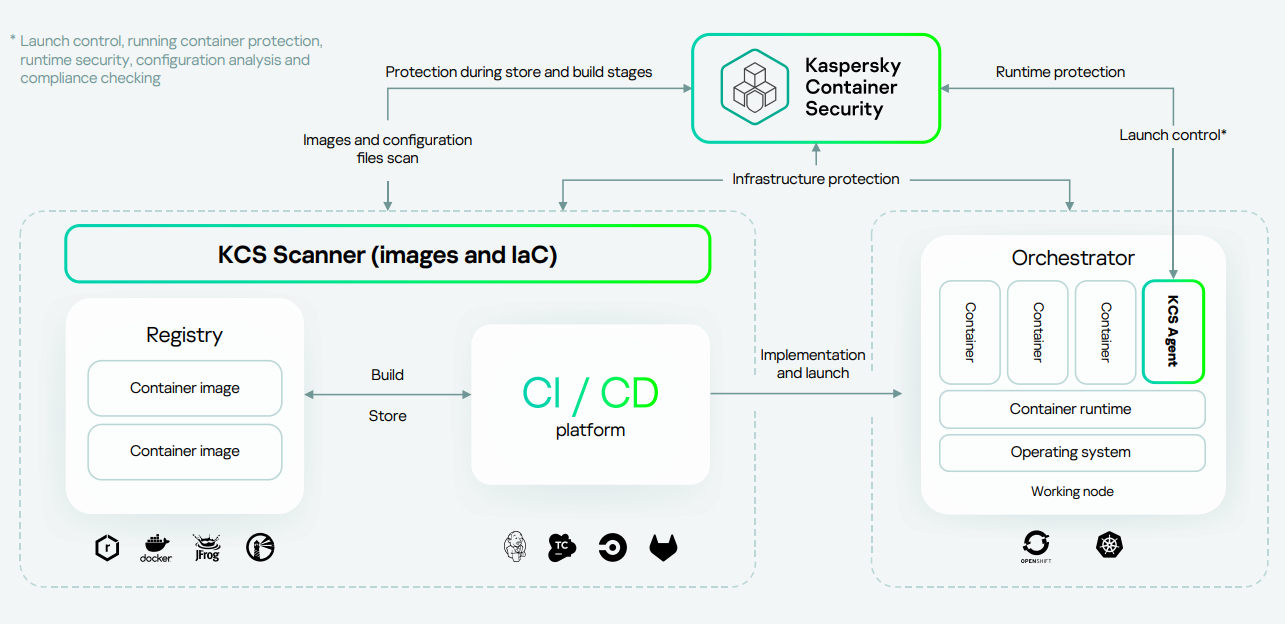
Kaspersky Container Security (KCS) enables protection at every stage of app design and operation. It consists of three components: KCS Agent, KCS Scanner, and KCS Control Server.
KCS Agent
Detects vulnerabilities at container, cluster, and orchestrator levels, ensuring runtime security. Installs into the cluster as a stand-alone container.
KCS Scanner of images and infrastructure
Checks the image registry for relevance and security. The scanner also checks images as part of the CI process, thus reducing the build stage risks. Installs into the cluster with the orchestrator's server components.
KCS Control Server
Responsible for monitoring the status of the solution components and interaction between them, as well as aggregation of information on detected events. Installs into the cluster with the orchestrator's server components.
Integration into the development process


![]()
![]()
![]()