Kaspersky Smart Technologies and ICS Security Assessment
Enhancing security of embedded systems
![]()
Overview
Embedded systems are becoming increasingly complex. Industry has made huge strides, from highly specialized microcontroller-based components to complex interconnected solutions built on third-party SoC platforms with real-time or Linux-based operating systems communicating with each other via dozens of different protocols. This kind of rapid evolution brings tremendous versatility, but it also comes at a price: the introduction of common computing platforms in embedded systems has brought its inherent threat landscape with it.
Kaspersky Lab offers a set of proactive security assessment services for vendors of embedded systems who want to enhance their security operations and take a pre-emptive approach against advanced threats.
Service Scope and Options
![]()
Embedded Devices Security Assessment
Security-level evaluation of the hardware and software components of embedded devices to identify potential vulnerabilities, misconfigurations and design issues that could be used by malefactors to compromise normal operation of the platform.
![]()
Application Security Assessment
Detailed security analysis of applications used to control and monitor the operation of embedded systems, including static and dynamic analysis of the application’s source code and architecture.
![]()
Penetration Testing
Analysis of the security of IT infrastructure that enables the operation of embedded systems, attempting to bypass security controls on behalf of various types of intruders aiming to obtain maximum possible privileges in important systems.
![]()
Comprehensive Reporting
A summary report detailing all discovered vulnerabilities and security flaws, with actionable recommendations for immediate resolution
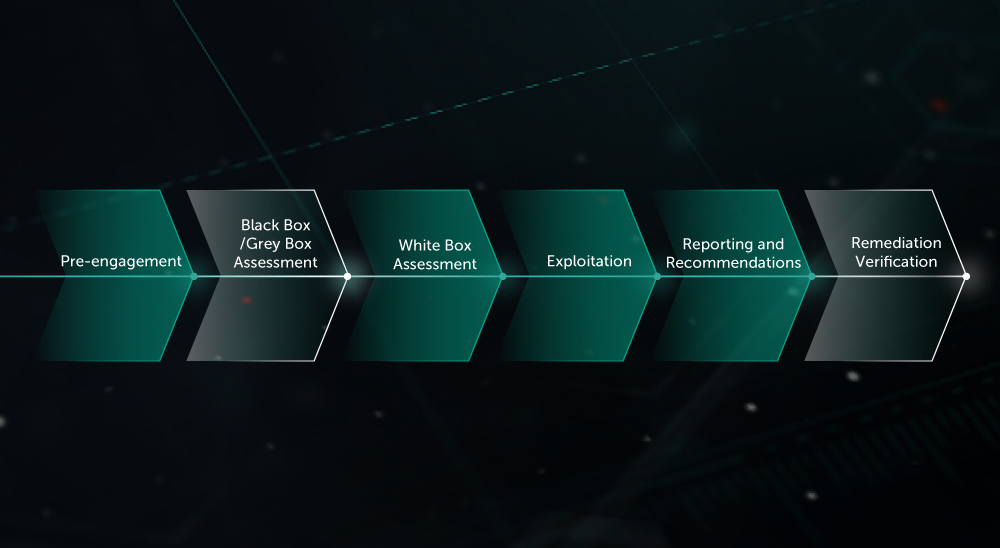
Embedded Device Security Assessment
A comprehensive security-level evaluation of hardware and software components of embedded devices. The aim is to identify potential vulnerabilities, misconfigurations and design issues that could be used by criminals to compromise normal operation of the platform.
The following types of activities can be conducted with this service (depending on the type of system and access level granted):
- Threat modelling according to business logic and use cases
- Manual and automated identification of vulnerabilities, including research aimed at finding vulnerabilities
- Firmware and application source code analysis using static, dynamic and interactive approaches
- Security assessment of underlying communication protocols and existing security controls
- Radio channels security assessment, including mobile and wireless networks (2G/3G/4G, Wi-Fi, Bluetooth, ZigBee, Z-Wave, NFC, etc.)
- Configuration analysis for operating systems and application components
- Evaluation of implemented security measures
- Exploitation of the revealed vulnerabilities and attack demonstration
- Preparation of a technical report containing detailed information on findings, recommendations, and conclusions on the likelihood of different types of threats.
If our experts discover zero-day vulnerabilities, they will provide advisories to software vendors and at the same time follow a strict responsible disclosure policy. We also develop recommendations to mitigate any impact related to discovered vulnerabilities, until the vendor releases a security update.
Application Security Assessment, Web Application Security Assessment, and Mobile Application Security Assessment
These assessments involve a detailed security analysis of applications used to control and monitor the operation of embedded systems. It includes static and dynamic analysis of the application’s source code and architecture. Kaspersky Lab’s experts will discover any vulnerabilities that may allow an intruder to bypass authentication and authorization procedures, raise privileges, or bypass security controls or fraud detection.
The Application Security Assessment (using both automated and manual approaches) is aimed at detection of vulnerabilities leading to:
- Gaining control over the application
- Attacks against the application’s clients
- Denial of service of the entire application, or partial denial of service (blocking access of individual users)
- Obtaining important information from the application
- Influencing data integrity
During the analysis, our experts will not only discover configuration flaws and vulnerabilities in obsolete software versions, but will also deeply analyze the logic behind the processes performed by the application, evaluate the presence and quality of security mechanisms and perform security research aimed at identifying new vulnerabilities. Special tools for attack automation can be developed by request to demonstrate the impact of an attack and validate findings.
Penetration Testing
Penetration Testing involves analyzing the IT infrastructure for the presence of security flaws that may allow external and internal intruders to operate embedded systems including testing attempts to bypass security controls to obtain the maximum possible privileges in critical systems.
Depending on your needs and the specifics of your systems, you can choose from various types of IT infrastructure security assessment services – or combine them:
- External penetration testing – security assessment from the Internet without any preliminary knowledge of your system.
- Internal penetration testing – security assessment on behalf of an internal attacker, for instance a visitor having only physical access to your office, or a contractor with limited access to certain systems.
- Wireless networks security assessment – our experts will visit your site and analyze Wi-Fi security controls.
Security Assessment Reporting
Once the security assessment has been completed, customers receive a report containing detailed technical information:
- High-level conclusions on the current security level of the systems in the scope.
- Description of the service methodology and process.
- Detailed description of detected vulnerabilities, including severity levels, exploitation complexity, possible impact on the vulnerable system, and evidence of the existence of the vulnerability (where possible).
- Recommendations on eliminating vulnerabilities, including changes in configuration, updates, changing source codes, or implementing compensative controls where vulnerability elimination is not possible.
Pricing Notes:
- Pricing and product availability subject to change without notice.